In the previous lesson, we discussed IP addresses. Remembering the IP addresses is difficult. It’s not easy to remember all the IP addresses that we need for our daily use. Domain name service (DNS) allows us to use “easy to remember” names instead of memorizing IP addresses. For instance, instead of remembering 173.194.44.230 we can use www.google.com
DNS is like a phone book for the Internet. There is a name for each website and instead of a phone number, there is an IP address that exists for each website. DNS uses a distributed database system where each organization is responsible to maintain data for its own domain.
DNS has a hierarchical nature. There is a root DNS server which provides high-level information for individual DNS server to tell them what server is responsible for all .net domains or what server is responsible for all .com domains. Similar servers exists for each top-level domains ( .com , .net , .org). Each of these servers then distributes authoritative for specific domains to the name servers run by the organizations that own the domain or their Internet Service Provider (ISP) . for instance yahoo.com runs its owns DNS servers. Yahoo DNS servers will have all information about yahoo subdomains such as www.yahoo.com or mail.yahoo.com
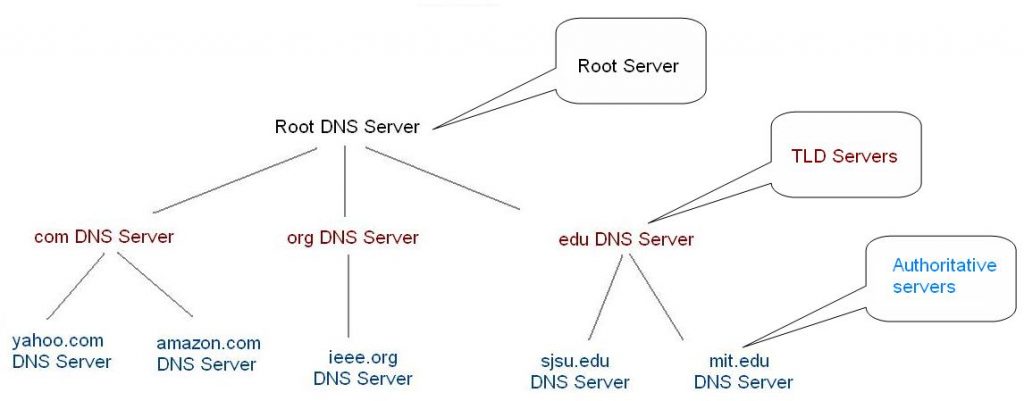
Each organization might use a relative extension after its domains. For example, MIT is an educational institute which uses .edu extension at its domain ( mit.edu ) you can find a more detailed list of top-level domain list at ICANN .
When a DNS server receives a request from a client on its network from a domain which it is not authoritative for, It has two options: (A) Check the DNS cache. (B) Perform a hierarchical lookup.
Each DNS server keeps a cache of recently looked up domains. For better understanding, I will give you an example. For example, you are on the AOL network and you try to access the sadeghian.us website. So first you need to enter sadeghian.us in the web browser. then your computer will look up in the local DNS server. DNS server of your company runs by aol.com so it is not authoritative for the sadeghian.us domain. However, the DNS server might recently ask the same question from another DNS server for another user which trying to access the same website. So the first place it will lookup is the cache (memory) to see if it has the answer. If it didn’t find the answer in the cache, it will go to perform a hierarchical lookup.
hierarchical lookup checks with the root server to find the responsible DNS server for the “.com” domains. then it will contact one of those .com domain servers and ask which server is responsible for sadeghian.us. Afterward, it will contact that name server to find the specific IP address for www.sadeghian.us.
There are some security threats related to DNS such as:
- DNS cache poisoning (DNS spoofing): In this type of attack, the attacker tries to insert false records into a DNS server cache. For instance, an attacker might insert false DNS records instead of HSBC DNS records inside Aol DNS servers. As a result, all users who access the internet form the AOL server will see the fake HSBC website. This attack might be used to collect bank credentials, which later might be sold on the black market. One of the challenges about finding the cache poisoning attack is that the attack is limited to a specific server and this makes it hard to detect the attack. For instance, in the above example while AOL server users are accessing a fake HSBC website other people who use another server from around the world still can access the legitimate website.
- Typosquatting: This attack which also known as URL hijacking is relied on the user mistake in typing the domain address of the website. This might happen when the user unconsciously types one additional character or one less character than a real domain address. In this type of attack, the attacker buys domain names which are similar to a famous website domain address and he hopes one day a user because of mistake in typing redirect to his website. For example, if the user wants to access twitter.com he might write twiter.com or twiiter.com or twiterr.com which in case these domains are registered by a malicious third party, the user will be redirected to there. And that site with a fake page similar to the legitimate website might be used to do a Phishing attack to collect user information.
_ \ \ | __| | | . | \__ \ ___/ _|\_| ____/